 OSEP is a new cert. It was introduced by Offsec in November 2020 and it immediately felt like they would finally address the gap in their certs for the netsec area, while simultaneously throwing Offsec in the market of Red Team related certs/courses.
OSEP is a new cert. It was introduced by Offsec in November 2020 and it immediately felt like they would finally address the gap in their certs for the netsec area, while simultaneously throwing Offsec in the market of Red Team related certs/courses.
Read more…
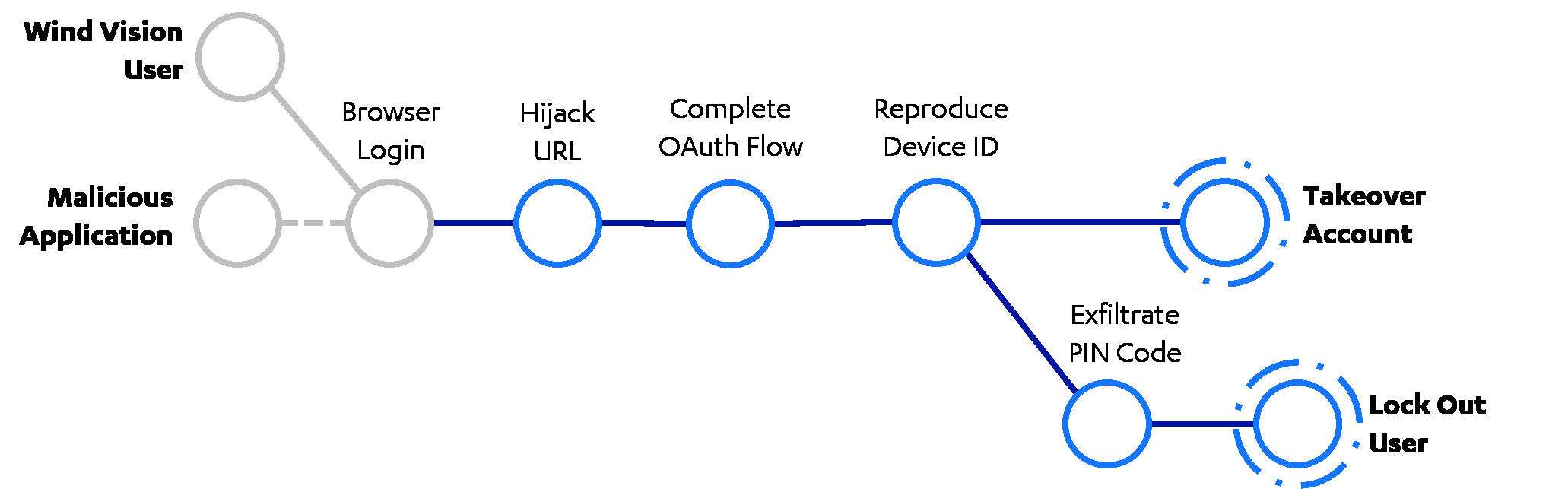 Last year, while playing around with the Wind Vision mobile application, I noticed that the login process was implemented in a potentially risky way. I decided to take a look, which led to an in-depth analysis over the course of two months. In brief, I found a way for a malicious app to takeover the victim's Wind Vision account, by chaining a series of otherwise unimportant bugs, starting with just one wrong click. As a note, the issues have already been responsibly disclosed to Wind and the software vendor, and the app was recently updated to prevent the attack.
Last year, while playing around with the Wind Vision mobile application, I noticed that the login process was implemented in a potentially risky way. I decided to take a look, which led to an in-depth analysis over the course of two months. In brief, I found a way for a malicious app to takeover the victim's Wind Vision account, by chaining a series of otherwise unimportant bugs, starting with just one wrong click. As a note, the issues have already been responsibly disclosed to Wind and the software vendor, and the app was recently updated to prevent the attack.
This post aims to highlight the caveats of authentication flows and inter-process communications (IPC) for mobile application developers, and to also outline the overall risk imposed by these flaws to end users.
Read more…
 Wind Vision is a digital television service offered by WIND Hellas, a Greek telecommunication provider, allowing for streaming of digital content. The Wind Vision mobile application, available for Android and iOS devices, allows users to watch TV 'on the go' from their smartphone devices.
Wind Vision is a digital television service offered by WIND Hellas, a Greek telecommunication provider, allowing for streaming of digital content. The Wind Vision mobile application, available for Android and iOS devices, allows users to watch TV 'on the go' from their smartphone devices.
The Wind Vision Android application is available on Google Play Store. The latest version currently available at the time of writing (10.0.16) was found vulnerable to four security issues. The vulnerabilities could be combined into an attack chain that would allow a malicious third party application to takeover a victim user's account. After compromising a legitimate account, an adversary could proceed to download and watch TV content abusing the victim’s subscription, or deny the victim access to their account by changing the PIN code and replacing registered devices.
Read more…
 In this article I'll describe a solution to bypass country restrictions imposed by web (or mobile) apps we're tasked to pentest, using a virtual machine (VM) running our VPN of choice. You know, these cool ones that provide multiple gateway servers across the globe to choose from, like F-Secure's FREEDOME.
In this article I'll describe a solution to bypass country restrictions imposed by web (or mobile) apps we're tasked to pentest, using a virtual machine (VM) running our VPN of choice. You know, these cool ones that provide multiple gateway servers across the globe to choose from, like F-Secure's FREEDOME.
Read more…
 Xiaomi Second Space replaces Android User Profiles on MIUI devices. It allows for a Primary (admin) and a Second user to switch profiles via an icon on the homescreen or from the lock screen. Both user spaces can be protected by a PIN or password.
Xiaomi Second Space replaces Android User Profiles on MIUI devices. It allows for a Primary (admin) and a Second user to switch profiles via an icon on the homescreen or from the lock screen. Both user spaces can be protected by a PIN or password.
A method was discovered in the Xiaomi MIUI System, that allows a user to switch between spaces without providing a password or PIN. This requires Second Space and Password / PIN screen lock to be enabled along with USB debugging.The vulnerability is triggered by an ADB command which can immediately switch space without requiring input of the password.
Read more…
 OSEP is a new cert. It was introduced by Offsec in November 2020 and it immediately felt like they would finally address the gap in their certs for the netsec area, while simultaneously throwing Offsec in the market of Red Team related certs/courses.
OSEP is a new cert. It was introduced by Offsec in November 2020 and it immediately felt like they would finally address the gap in their certs for the netsec area, while simultaneously throwing Offsec in the market of Red Team related certs/courses.

